OAUTH
Single Sign-On (SSO) with OAuth is a framework that allows users to log in to multiple applications or services using a single set of credentials. OAuth is primarily focused on granting access to resources (like user data) on behalf of a user, while SSO focuses on authentication.
Google Cloud Service offers Cloud Identity as an Identity Provider (IdP) supporting OpenID Connect (OIDC) for streamlined Single Sign-On (SSO) access to Wyn Enterprise application users. To enable SSO with the Wyn Enterprise application, ensure you have installed version 6.0 or above, and have access to the Google Cloud Platform with a user account in Cloud Identity or Google Workspace.
Switch to the Admin Portal and follow the below instructions to configure the CAS authentication protocol in Wyn Enterprise,
Navigate to Configuration >> System Configurations >> SSO Settings and select the OAUTH option from the Authentication Protocol dropdown.
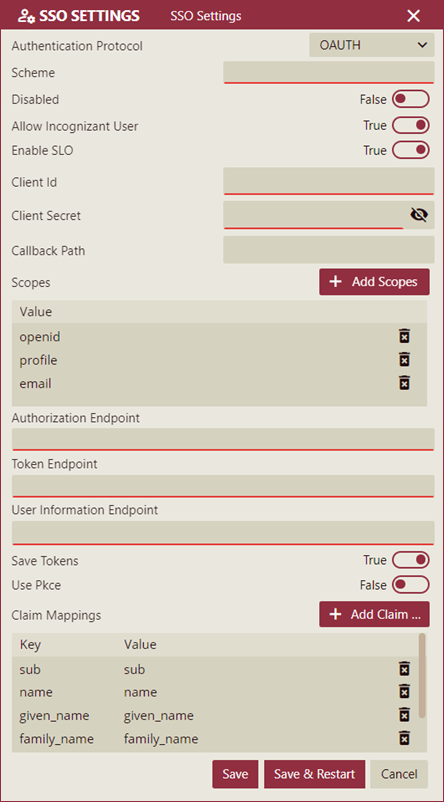
Add the OAUTH settings that appear in the SSO Settings tab. The OAUTH authentication settings are listed and described below.
Setting
Description
Values
Authentication Protocol
Authentication Protocol parameter is used to specify the protocol used to authenticate users for SSO.
None, CAS, OIDC, OAUTH
Scheme
Scheme parameter is an identifier of the authentication provider.
CAS, MicrosoftAzureAD, AWSCognitor, MyTestingIdentityProvider, etc.
Disabled
Disabled parameter is used to disable the SSO function.
True or False. The Default value is False.
Allow Incognizant User
Allow Incognizant User parameter is used to allow users not existing in the Wyn Enterprise application to log in to the application.
True or False
Enable SLO
Enable SLO is used to enable or disable a single logout feature when users log out from the Wyn Enterprise application. By default, this value is set to True.
True or False
Client Id
Client Id parameter specifies the public identifier for the user required for OAuth flows.
For Amazon Incognito, values are available in your user pool. For OKTA, values are available in your OKTA app settings.
Client Secret
Client Secret parameter specifies a secret code used by the user to exchange an authorization code for a token. ClientSecret should be kept confidential.
For Amazon Incognito, values are available in your user pool. For OKTA, values are available in your OKTA app settings.
Callback Path
Callback parameter specifies a base URL where the IDP response is sent upon user authentication. Callback parameter is used in the SSO configuration settings with Amazon Cognito Service.
Redirect URI specified in the AWS app settings or the default value is /signin-oidc.
Scopes
Scope parameter is used to customize data requests to a third-party application.
For OKTA: openid, profile, and email. For AWS: openid, profile, email, and phone.
Authorization End Point
Authorization End Point is the URL used for authentication and authorization.
/oauth2/authorize
Token Endpoint
Token Endpoint is a dedicated node used to issue access tokens after successful authentication of the OAUTH client.
[issuer-url]/token
User Information Endpoint
User Information Endpoint is a URL used to retrieve consented claims, or assertions about the logged-in end-user.
[issuer-url]/userinfo
Save Tokens
Save Tokens property is used to save the tokens. By default, this property is set to True.
True or False
Use Pkce
Proof of Key for Code Exchange is an extension to the authorization code flow to securely perform the OIDC exchange from public clients.
True or False
Claim Mappings
Claims are used to determine the authenticated users' information such as name, phone number, email, roles, etc. A claim mapping item consists of a Key and a Value where the Key represents the user context in Wyn Enterprise, and the Value represents the user context from the authentication provider. Click the + Add Claim button to add claims and set the Key and Value fields.
id, profile, status, transitioningtostatus, created, activated, statuschanged, lastlogin, lastupdated, passwordchanged, type, realm, realmid, password, credentials, _links, _embedded, class, classloader, custom_name
You can also manually configure the OAUTH Single Sign-on settings using the Wyn.conf file located in the Wyn system folder. See the Google Cloud Service help article for more information on the manual configuration of the OAUTH authentication protocol for SSO in Wyn Enterprise.